Unmasking the New Tactics: How Scammers Bypass iPhone Safety Features
In an age where smartphones serve as our lifelines, the security of these devices has never been more critical. iPhones, known for their robust safety features, have become a primary target for scammers who continuously evolve their tactics to exploit vulnerabilities. This article explores the innovative methods scammers use to circumvent iPhone security measures and provides essential advice on how users can protect their devices.
The Increasing Sophistication of Scammers
Scammers have always sought ways to deceive users, but the growing trend of sophisticated tactics raises alarms. With the continual updates to iPhone security, one might assume that fraudsters would struggle to find new methods. However, this is far from the truth. Many scammers have become adept at leveraging social engineering, technical exploits, and even psychological manipulation to bypass these safety features.
Common Tactics Employed by Scammers
Understanding the tactics used by scammers is the first step toward protecting oneself. Here are some of the most common methods they employ:
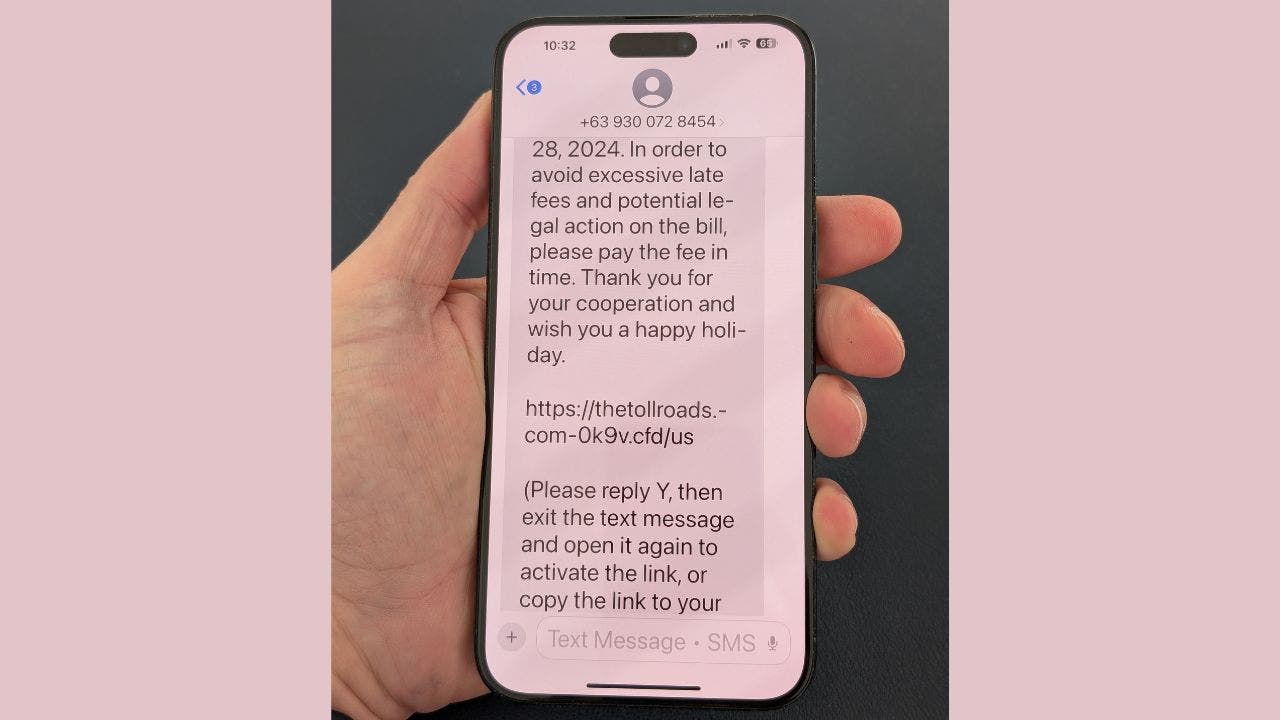
- Phishing Attacks: Scammers often use emails or text messages that appear to be from legitimate sources, such as Apple or financial institutions. They create a sense of urgency, prompting users to click on malicious links that lead to fake login pages.
- Impersonation: Fraudsters may impersonate a trusted contact or a legitimate organization. They exploit this trust to request sensitive information, such as passwords or verification codes.
- Malware and Spyware: Although iPhones are generally resistant to malware, some sophisticated attacks involve tricking users into downloading malicious software disguised as legitimate apps.
- SIM Swap Scams: In a SIM swap attack, scammers convince mobile carriers to transfer a victim’s phone number to a SIM card they control. This grants them access to two-factor authentication codes and sensitive accounts.
- Fake Tech Support: Scammers may call or message individuals claiming to be from Apple Support, offering assistance for non-existent issues. They often ask for remote access or personal information under the guise of troubleshooting.
How Scammers Bypass iPhone Security Features
Despite the security measures Apple implements, scammers have found ways to exploit them. Here’s how they do it:
Social Engineering Techniques
One of the most effective tactics involves social engineering. Scammers are skilled at manipulating emotions and creating scenarios that prompt users to act impulsively. For example, they may pose as a friend who has lost their phone, urging the victim to share their verification codes.
Exploiting Software Vulnerabilities
While Apple regularly updates its software to patch vulnerabilities, some flaws may remain undiscovered for a time. Scammers can exploit these vulnerabilities before they are addressed. Their tactics might involve using specially crafted websites or apps that take advantage of these weaknesses.
The Role of Public Wi-Fi Networks
Public Wi-Fi networks pose another risk. Scammers often set up fake networks that mimic legitimate ones. When users connect to these networks, fraudsters can intercept data, including login credentials and sensitive information. This tactic is particularly dangerous because many users assume public Wi-Fi is secure.
Protecting Yourself and Your iPhone
While scammers are constantly evolving their tactics, there are proactive measures you can take to safeguard your device and personal information:
- Enable Two-Factor Authentication: This adds an extra layer of security to your accounts. Even if a scammer obtains your password, they would still need your verification code to access your account.
- Be Cautious with Links: Avoid clicking on links in unsolicited emails or messages. Instead, navigate directly to the website by typing the address into your browser.
- Use Strong, Unique Passwords: Ensure your passwords are complex and not reused across multiple accounts. Consider using a password manager to help manage them securely.
- Regular Software Updates: Keep your iPhone updated with the latest software. These updates often include crucial security patches that protect against known vulnerabilities.
- Avoid Public Wi-Fi for Sensitive Transactions: If you must use public Wi-Fi, consider using a Virtual Private Network (VPN) to encrypt your data.
Recognizing the Signs of a Scam
Being able to recognize the signs of a scam can further protect you from falling victim. Here are some red flags to watch out for:
- Urgent Requests: Scammers often create urgency. If someone is pressuring you to act quickly, take a step back and assess the situation.
- Unsolicited Contact: Be cautious if you receive unexpected calls or messages, especially if they request personal information.
- Suspicious Links: Links that seem odd or poorly formatted can lead to phishing sites. Always verify the URL before clicking.
- Too Good to Be True Offers: If an offer sounds too good to be true, it likely is. Scammers often use enticing offers to lure victims.
Conclusion
As technology advances, so do the tactics of scammers. The innovative methods they employ to bypass iPhone safety features are a growing concern for users everywhere. However, by understanding these tactics and implementing robust security measures, you can protect yourself and your device from potential threats. Awareness and vigilance are your best allies in this ongoing battle against fraud.
Stay informed, stay secure, and remember that the best defense against scams is knowledge. By arming yourself with information and being proactive, you can enjoy the benefits of your iPhone without falling victim to the ever-evolving landscape of scams.
See more Future Tech Daily